THE WHYS AND WHEREFORES OF AUTOMATING PRIVILEGED TASKS

A task can be defined as:
noun 1. A piece of work that needs to be done regularly.
verb 2. Assign a piece of work to.
IT operations teams are often inundated with menial, regular and repetitive tasks (e.g. trigger events, running daily monitoring activities and starting services) that can not only be damaging to the business when done incorrectly, but also hinder productivity. By limiting the number of tasks assigned to IT and enabling greater access to automation capabilities, performance and productivity can be significantly improved. In parallel, it’s important to protect your environment from risks such as the abuse or misuse of privileged access (insider threats), service outages caused by human error (typos) and third-party/remote vendor vulnerabilities (external threats).
Automation can be defined as:
noun 1. The technique, method, or system of operating or controlling a process by highly automatic means, as by electronic devices, reducing human intervention to a minimum.
I recently addressed the importance of locking down the remote vendor attack pathway, as this is often an easy target for cyber attackers. By automating privileged tasks (any task to be performed by a privileged user), you can lessen potential vulnerabilities in process workflows both utilized by internal users and remote vendors alike. Once you fully automate a privileged task, you’re not only simplifying privileged account security processes, but also helping to ensure your remote vendors (who might have access to critical servers, endpoints and applications) will not inadvertently make an error that could lead to a serious security risk.
Additionally, in the DevOps world, orchestration tools are automating tasks across workflows, taking this role from IT operations and vendors – even for some systems that are no longer in existence. In the on-premises world, organizations still rely on vendors and support staff to perform tasks on an ad-hoc, often sporadic basis. Ideally, organizations should allow all of these tasks to be performed while a complete and correlated audit trail is generated automatically.
CyberArk solutions enable audit and operations teams to monitor and record the task management and automation of related activities as well as promote user accountability across the board. Users can automate maintenance and provisioning of tasks, (re)start and stop services, and only launch the applications or clients necessary to perform the task at hand – and nothing else. Users can also automate deployments through remote SSH command execution on target systems in both on-premises and cloud environments – all while maintaining the highest security standards. This functionality enables users to place restrictions on what privileged users are allowed to do with an organization’s most critical assets.
So How Does it Work?
Let’s walk through a simple example. A local Windows Server Administrator account has been on-boarded into the CyberArk Vault, and the usage of this privileged account has been limited to only a handful of allowed operations.
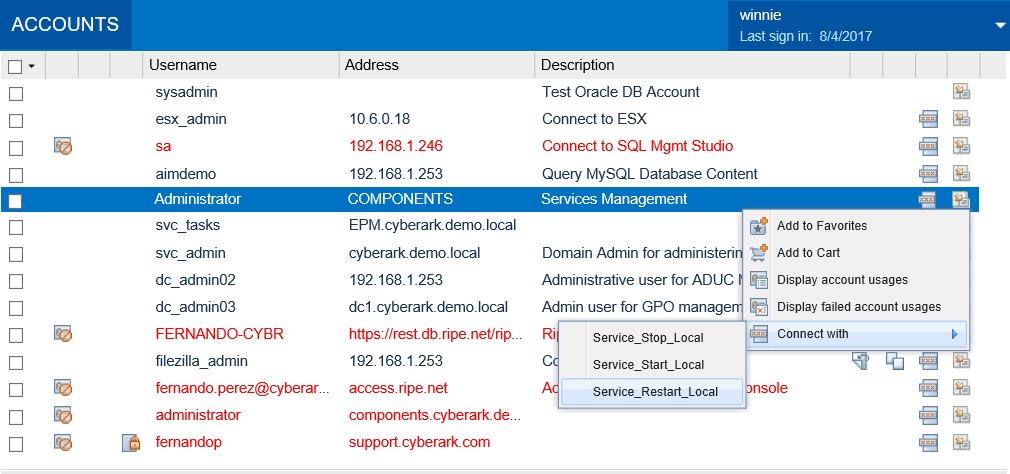
Full access to the server is not permitted, the user can only manage a list of services running on that server.
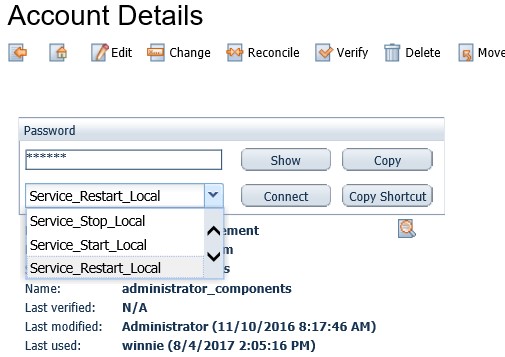
The user selects “Restart Service” and is then prompted to select the service to be managed, which can be pre-populated or added as a part of a drop-down list to further limit the control the user has over this account and the server.
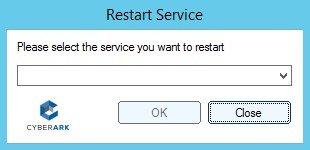
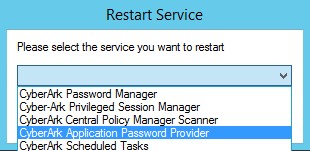
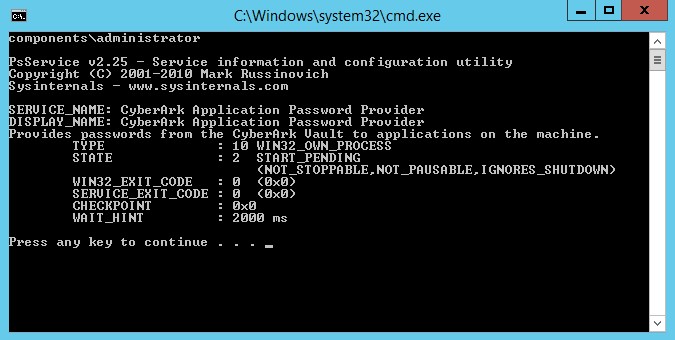
After the user clicks ‘OK,’ the service will restart. Through the CyberArk Privileged Session Manager, a full audit trail is created capturing the completed actions by each privileged user. Any abnormal behavior, abuse of privileges or any other privileged activities associated with that privileged task will be on record and immutably stored in a tamper resistant vault. Sessions can be monitored in real time or later reviewed by a member of the audit team to improve security and support compliance regulations.
Whether your tasks ‘need to get done regularly’ or they’re something you ‘assign a piece of work to,’ it’s in your best interest to introduce automation controls. The example above shows how easily this can be done. Organizations today mostly exist in a ‘do more with less environment’ so it’s a best practice to automate simple privileged tasks to keep a high level of security and enable IT operations teams to focus on workloads that deliver more value to the organization.
Learn more about privileged task automation and management by watching our on-demand webinar, “Curse of the Typo! Automate Repeated Tasks to Improve Efficiency and Reduce Risk Around User Mistakes.” You can review the on-demand version of the webcast at any time.
No comments:
Post a Comment